
As AI-powered tools become more advanced, traditional watermarking techniques are no longer sufficient to protect images from unauthorized reuse. Neural networks trained on millions of images, such as those used in popular watermark-removal platforms, can now identify, isolate, and reconstruct areas where logos or marks once appeared.
This shift creates significant risks for photographers, e-commerce sellers, real estate agencies, and any business relying on original images. When watermarks are easily removed, competitors can reuse commercial photos, causing brand confusion and potential loss of revenue.
Fact: Global e-commerce fraud losses are projected to exceed $343 billion by 2027, and image theft contributes heavily to this problem.
To address these challenges, a more sophisticated, multilayer watermarking strategy is required—one that is perceptible to users but difficult for AI systems to erase cleanly.
Four Technical Principles for AI-Resistant Watermarking
Modern content protection relies on engineering watermarks that disrupt the way AI algorithms detect patterns. Below are four proven methods that strengthen watermark durability, and tools such as SoftOrbits Batch Watermark Creator can be used as an example of software that applies these techniques at scale.
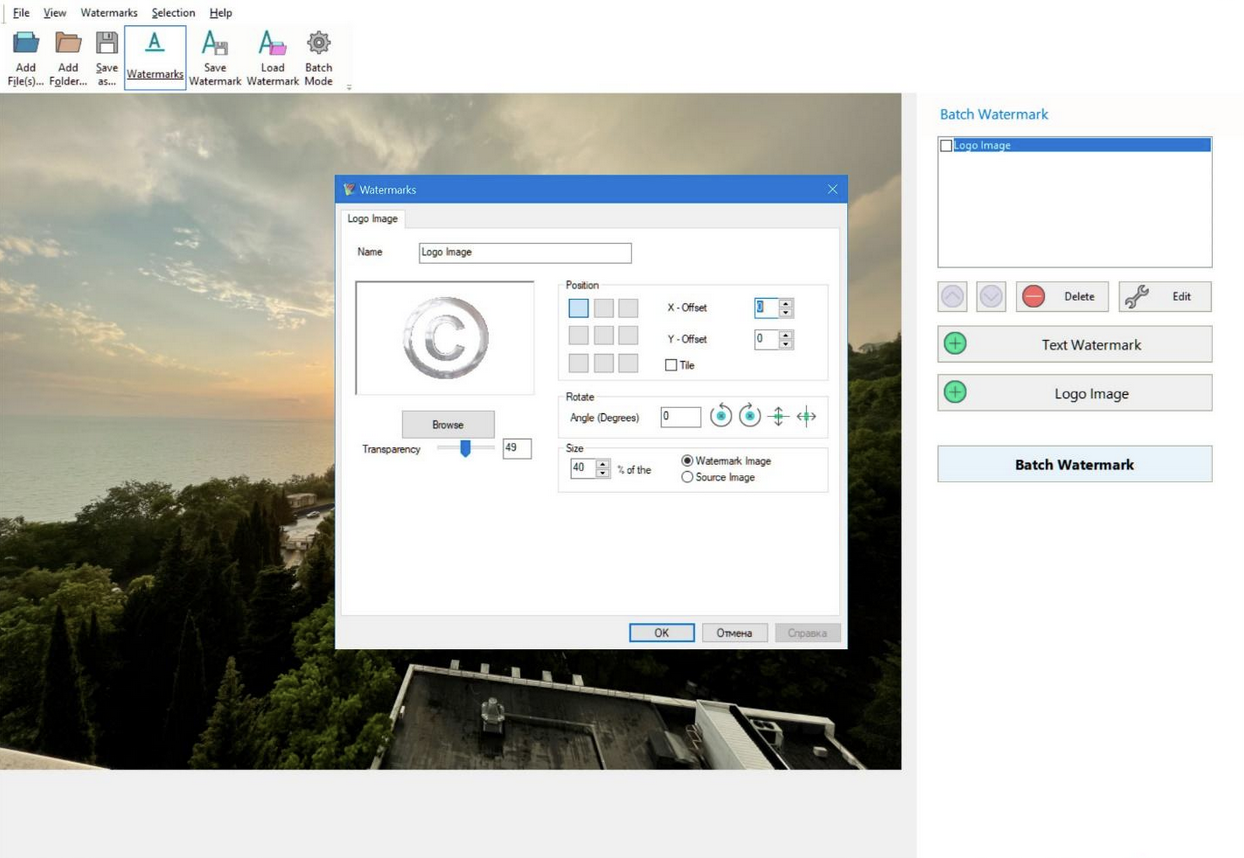
1. Tiling (Full-Image Repetition)
- Principle: The watermark is repeated across the entire image rather than placed only in one corner.
- Why it works: AI removal tools must reconstruct every portion of the image where the watermark appears. When the logo repeats dozens or hundreds of times, the algorithm must restore large areas rather than a single localized patch.
- Result: The probability of artifacts, distortions, or incomplete background reconstruction increases dramatically.
2. Distortion and Random Variation
- Principle: Watermarks are applied with changes in rotation, opacity, size, and position.
- Why it works: Neural networks typically identify patterns through repetition. When every watermark instance is slightly different, the model cannot easily generalize a universal removal method.
- Result: AI struggles to “lock onto” a predictable pattern, reducing the accuracy of automated cleanup.
3. Complex Textures and High-Detail Marks
- Principle: Watermarks incorporate gradients, textured fills, layered shapes, or color complexity.
- Why it works: AI performs best when boundaries between the watermark and the background are simple. Highly detailed textures make segmentation significantly more difficult.
- Recommendation: Place watermarks over high-detail areas (fabric, foliage, buildings) rather than blank backgrounds. Avoid overly transparent marks—semi-opaque or opaque patterns resist removal better.
4. Metadata Protection (EXIF and Rights Information)
- Principle: Embed ownership information, copyright notices, and timestamps into image metadata.
- Why it works: Metadata remains intact even if visible marks are altered or removed, providing legal proof of authorship and helping platforms verify rightful ownership.
- Recommendation: Always include metadata even when visible watermarks are present—it's an essential secondary layer of protection.
Practical Tips for Large Image Collections
Businesses managing extensive catalogs—such as real estate agencies, product listings, or photography archives—benefit from applying these principles consistently at scale.
Key best practices include:
- Batch watermarking: Ensures uniform protection across thousands of images.
- Combining techniques: For example, pairing a tiled pattern with a semi-transparent corner logo.
- Local processing: Helps maintain confidentiality, especially for unreleased or proprietary content.
- Routine updates: Periodically vary watermark design to prevent AI training bias over time.
Industry experts have noted a clear shift toward more complex watermark structures. Eugene Ustinenkov, CEO of SoftOrbits, summarized the challenge well: “In modern e-commerce, a semitransparent logo in the corner is just decoration. We developed batch watermarking tools to apply thousands of complex, distorted, tiled watermarks in one minute. Complexity is the best defender of commercial content.”
His observation reflects a broader trend across the digital imaging field: simple watermarks no longer provide meaningful protection against modern AI-driven removal tools.
Why Multilayer Watermarking Matters Today
AI watermark removal will continue to evolve, but multilayer strategies make unauthorized reuse significantly more difficult. Instead of relying on one easily recognizable logo, modern watermarking uses pattern complexity, randomness, and metadata to strengthen protection.
For creators and businesses, this means:
- Preserving brand identity
- Preventing unauthorized commercial reuse
- Protecting SEO value tied to original images
- Supporting legal claims when infringement occurs
In an era where AI tools can copy, enhance, and modify images instantly, thoughtful watermarking is no longer optional; it’s a necessary layer of digital security.
Conclusion
AI-driven watermark removal has changed the landscape of digital content protection. Simple corner logos are no longer enough to safeguard commercial photos or creative work. By applying multilayer techniques such as tiling, distortion, complex textures, and metadata preservation, creators can stay ahead of automated removal tools and maintain control over their intellectual property.
Whether managed manually or with batch-processing tools, consistent application of these strategies helps businesses protect brand value, reduce image theft, and reinforce legal ownership. As AI continues to advance, resilient watermarking isn’t just recommended; it’s essential.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment