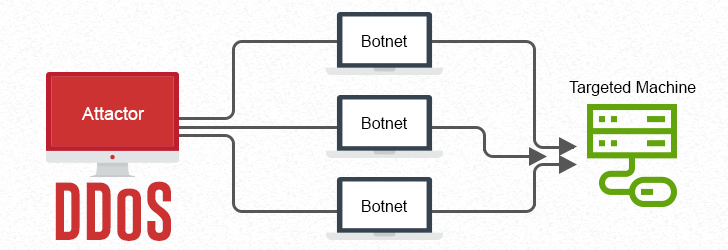
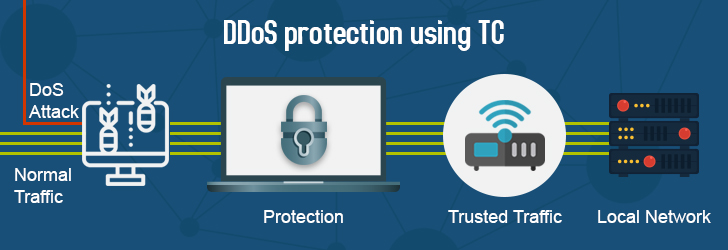
An IP stresser is a network load testing tool designed to evaluate the stability and performance of a server or online service under heavy traffic. Organizations use IP stressers to simulate peak loads, identify weak points, and ensure that a website or network can handle surges in requests without downtime.