A denial of service (DoS) attack is an explicit attempt made by an attacker to make victim's Internet resources unavailable to its intended audiences. The DoS attack is usually carried out by one machine connected to the Internet by exploiting known UDP and TCP vulnerabilities.
What is DDoS (Distributed Denial of Service) Attack?
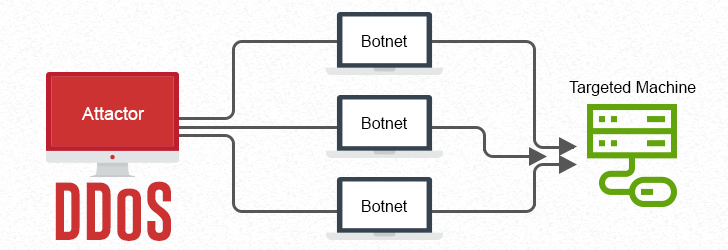
A distributed denial of service (DDoS) attack is a type of DoS attack carried out by multiple compromised computers to flooding victim's network in a way that victim's server cannot handle it. A DDoS attack involves 3 parties: an offender, helpers (or botnet) and a victim. The offender is the one who plots the attack, and helpers are the machines that are compromised by the offender to launch attack against a victim (the target). The offender commands the helpers to attack the victim's host at the precisely same time.
Why do people launch DDoS Attacks?
It is hard to pinpoint why some entities are targetted for DDoS attacks, and who's behind it. Since there are no hard evidences of why DDoS are happening, we'll rely on researches and theories based on some speculations to name a few reasons. Of the list below, some research states that hacktivism and vandalism were the main motivations for DDoS attacks.
- Hacktivism - Some hackers protest their critism by launching DDoS attacks against organizations or governments. Most government sites are attacked via DDoS one way or another by groups or even by another nation.
- Vandalism - Some hackers launch DDoS attack for no reason other than vandalising some known entities.
- Booter Services - A DDoS service offered by cyber criminals in exchange for money. A large number of DDoS attacks are carried out from purchased subscription. A research found that $100 can buy a week-long DDoS attack from a black market.
- Extortion - Although rare, there have been several DDoS attacks followed by a ransom note. An example of popular extortion attack is demanding 50% share of Manchester Based Online Casino using DDoS threat.
- Competition - A business owner sabatoshing it's competitor can benefit by damaging reputation of its competitor as well as gaining visitors to it's own site. Some online gambling sites are known to DDoS their competitors.
What is your protection plan?
There are three distinctive ways to protect DDoS attacks but their mileage vary significantly depending on the size and type of attacks being carried out.
1. Do-it-Yourself Mitigation
For small-scale DDoS attacks, you may mitigate youreself by securing your server with mod_evasive, mod_security and other WAF (Web Application Firewall) utilities offered by your operating system. Back in early 2000s, the size of DDoS attacks were pretty small and DIY methods may have worked but the size of DDoS attacks have magnified by hundreds in recent years and hence DIY methods rarely works these days.
- How to mitigate from DDoS with mod_security and mod_evasive?
- DDoS protection with APF, BFD, DDoS Deflate and Rootkit
- DDoS protection using TC (Traffic Control)
Some larger organizations attempt to deploy on-premise DDoS mitigation appliances such as F5 load-balancer and other DDoS detection devices, but installation and maintenance of such devices as well as building in-house expertise cost outrageously high compared to using ISP or Cloud based solutions.
2. Web Host provided Mitigation
Some web hosting companies offer virtual or dedicated servers with DDoS mitigation front-end. Some vendors deploy self-hosted DDoS mitigation appliances to defend their infrastructure while others partner with Cloud based DDoS Mitigation providers.
3. Cloud based DDos Mitigation Service Providers
Most small to medium size busniesses have limited resources to fend off a DDoS attack. A study from Incapsula states that nearly a half of DDoS attacks last between 6 and 24 hours. Depending on size of the attack, your team may not be able to fend off yourself in which case you'll have to rely on professional services.
For larger scale DDoS attacks, you'll have to turn to professional DDoS protection service providers. Even as tiny as 5Mbps attacks can't be handled by WAF utilities (see above) offered by most Linux distros.
There are a number of DDoS protection service providers, and picking anyone will most likely resolve moderate scale DDoS attacks. Most providers offer 7-day free trial, so you may use it to mitigate "under attack" situation, and seek long-term solution. Our experience with Incapsula mitigated one incident we've experienced with one of our sister site.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment