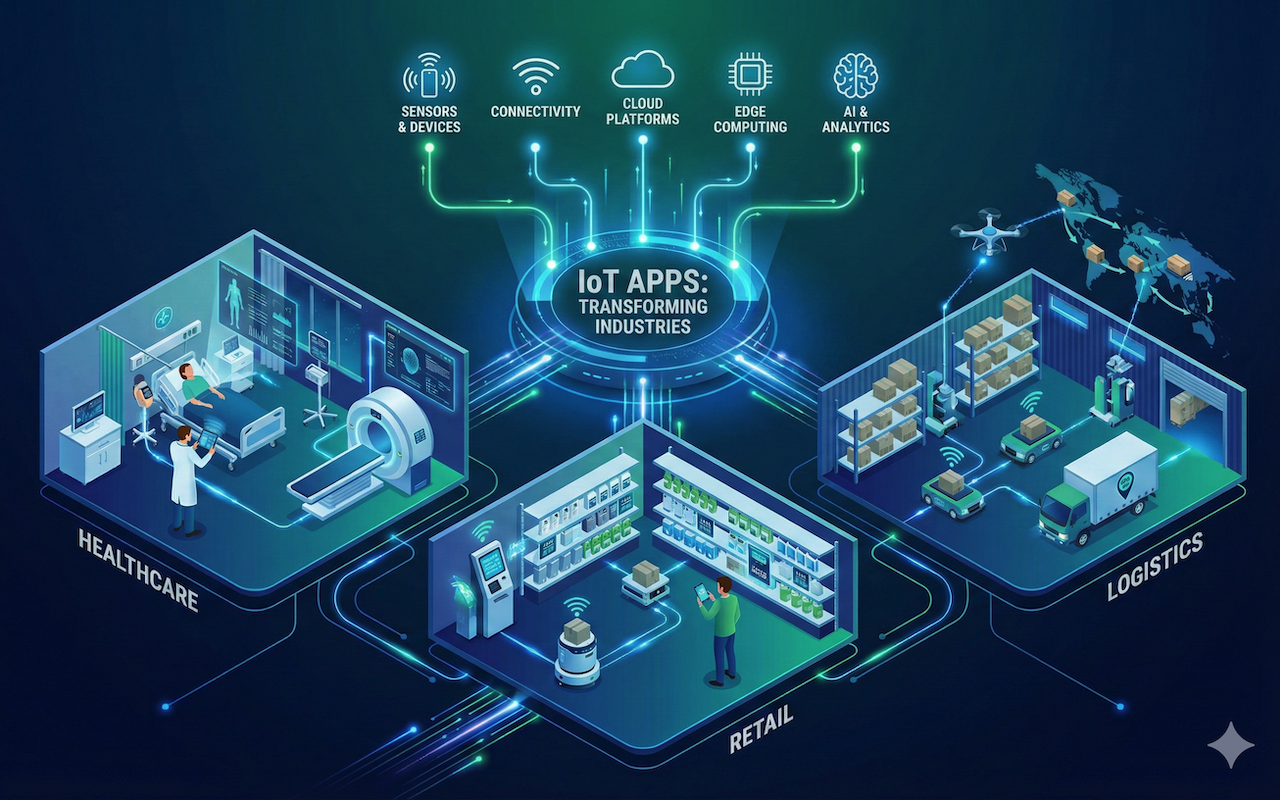
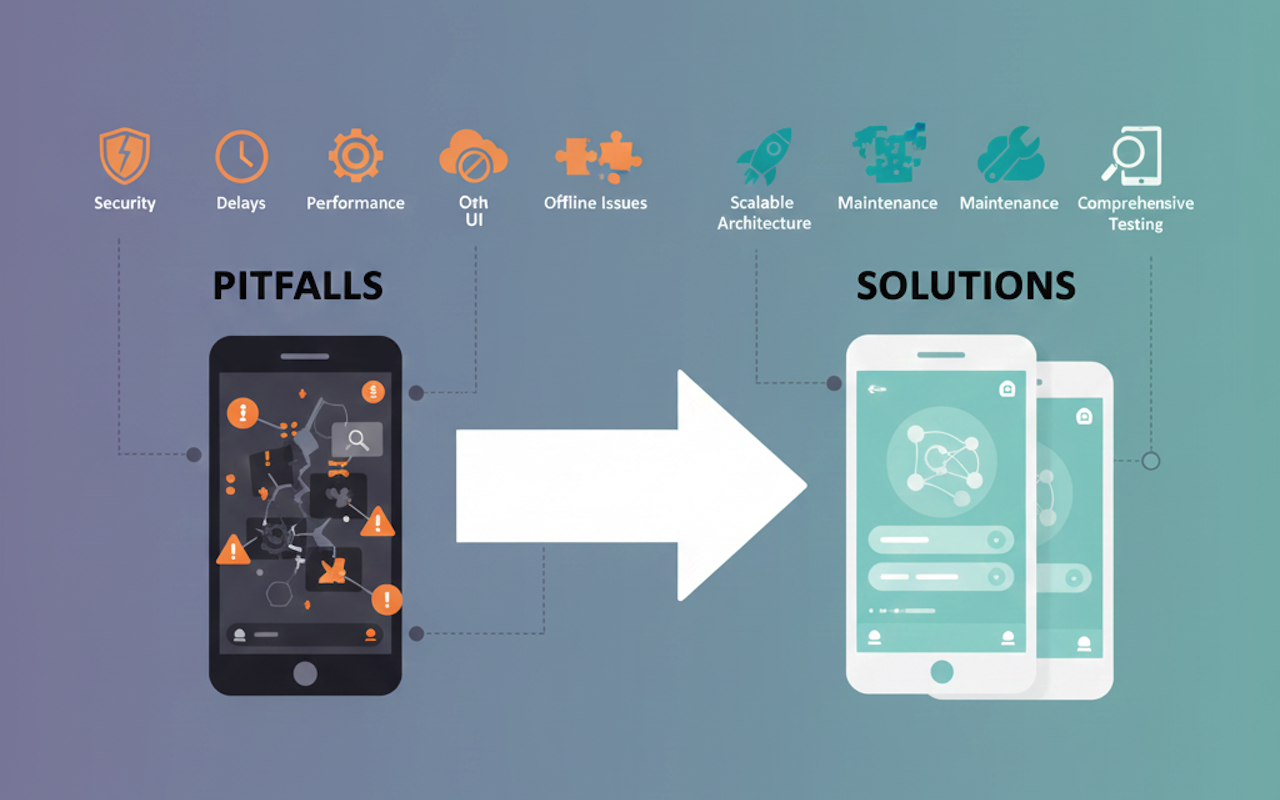
Blogging has gone through a enormous change in the final few a long time. Users don’t need data anymore; they need visual narrating, special formats, and posts that feel advanced and magazine-like. That’s where the magazine strip layout steps in. This slant has rapidly developed well known among bloggers, substance makers, and creators who need their posts to stand out in a swarmed advanced world. Instep of long, conventional passages, this layered and in vogue look instantly hoists your blog’s whole vibe.
[..]
Read more...