
Email is the primary identity used in modern digital life. It’s your login for accounts, your identity for services, and your communication channel for everything from banking to personal notifications. But using the same personal email address across dozens of websites comes with serious privacy and security risks.
With global data breaches rising over 8.2 billion records exposed in 2023, protecting your inbox identity has never mattered more. One simple strategy? Using temporary email addresses to limit exposure. This article explains why personal email reuse is risky and how Temp Mail provides an easy, effective layer of protection.
1. Why Your Personal Email is the Primary Target
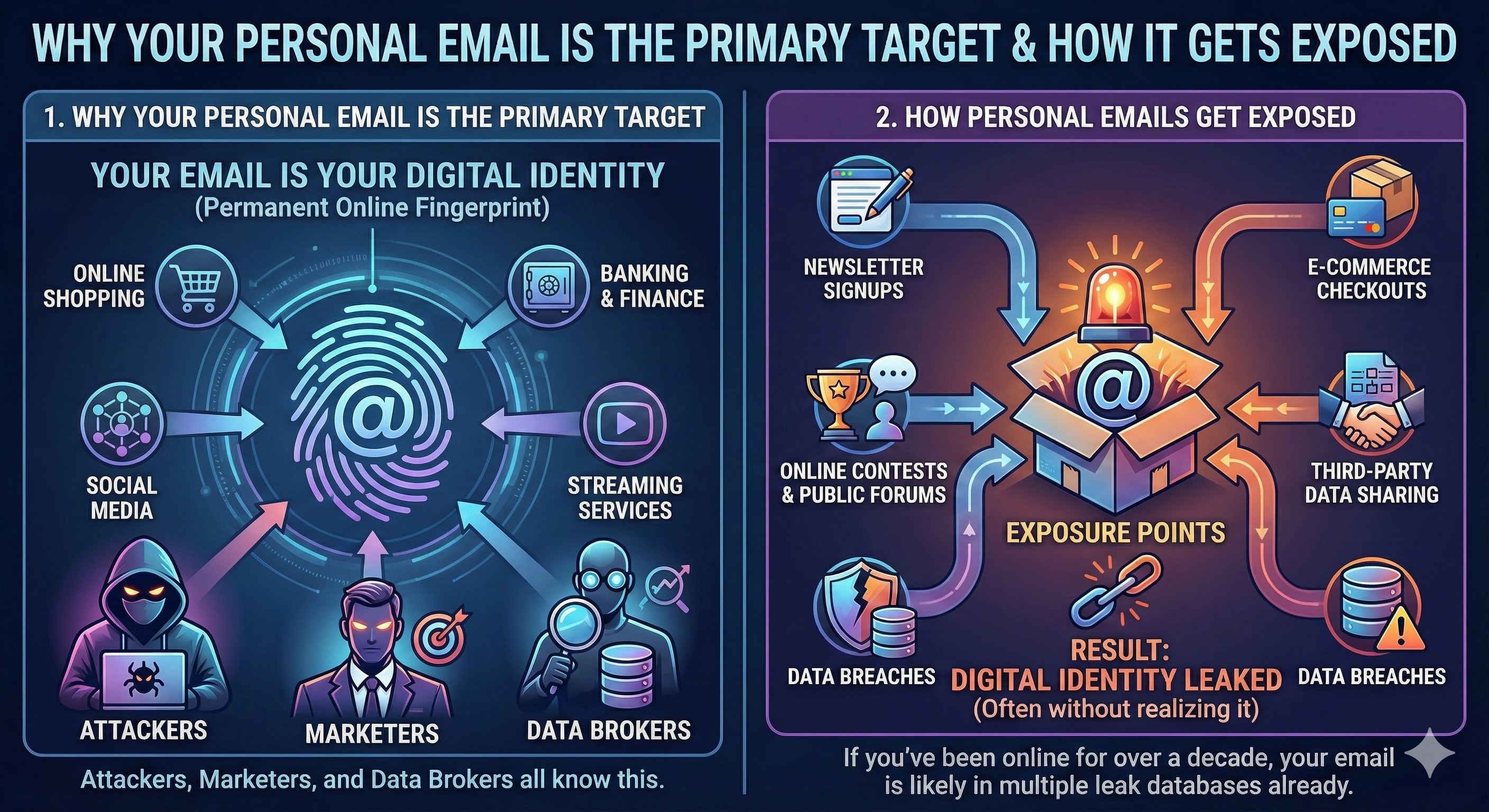
Your Email is Your Digital Identity
A personal email acts like your permanent online fingerprint. Nearly every major online activity, including shopping, banking, social media, and streaming, requires it.
Attackers know this. Marketers know this. Data brokers definitely know this.
How Personal Emails Get Exposed
Sharing your personal email online may seem harmless, but it’s one of the easiest ways your digital identity becomes exposed without you realizing it. The following are a few examples of how your email gets exposed.
- Newsletter signups
- E-commerce checkouts
- Online contests and public forums
- Third-party data sharing
- Data breaches from services you signed up for years ago
If you’ve been online for more than a decade, your email is likely in multiple leak databases already.
2. The Hidden Risks of Reusing Your Personal Email Across Websites
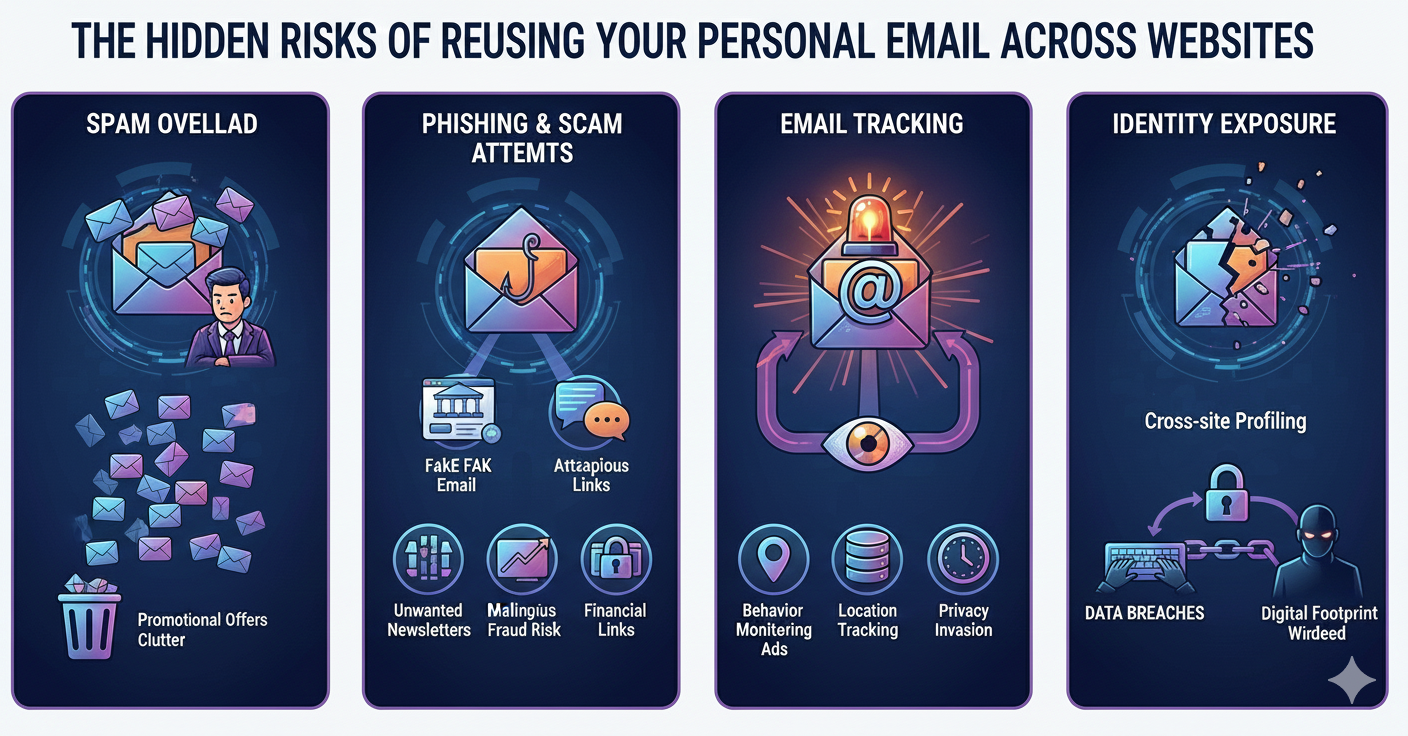
Spam Overload
Once your email enters marketing databases, it spreads fast. Data broker studies show that a single shared email address can attract 10–50 unsolicited senders within a year.
Sarah signs up for a “free PDF” from an unknown website using her primary email. Months later, she’s drowning in newsletters she never remembers subscribing to. The worst part? She can’t figure out which site leaked her information.
Phishing & Scam Attempts
Email leaks can lead to targeted phishing. Attackers enrich stolen emails with:
- Full names
- Locations
- Past purchases
- Social media profiles
In 2024, phishing accounted for over 36% of all cyberattacks.
Data Breaches
Your personal email is often the first data point exposed in a breach.
If the site used weak or reused passwords, attackers attempt credential stuffing: automated login attempts on banks, social media, and shopping accounts.
Email Tracking
Many newsletters track users with:
- Tracking pixels
- Unique identifiers
- Link fingerprinting
These reveal:
- When you opened the email
- Where you were located
- The device you used
- How many times you read it
For marketers, your email becomes a behavior map.
Identity Exposure
A personal email often contains your real name or leads back to social profiles, making it easy to connect your identity to everything you do online.
Alex signed up for a niche forum using his personal Gmail. Months later, an argument with a stranger results in that person Googling his email and finding his LinkedIn, workplace, and city.
3. How Temporary Emails Enhance Privacy and Reduce Security Threats

Temporary or disposable email addresses are single-use inboxes that exist for minutes or hours. They’re perfect for quick signups with no long-term commitment.
Breaking Identity Links
A temporary email breaks the tie between:
- Your real identity
- Your online browsing habits
- Your long-term email account
Websites cannot build a deep profile tied to your true inbox.
Spam Prevention
Promotional blasts and marketing emails are confined to the disposable inbox, keeping your real inbox clean.
Damage Control During Breaches
If a temporary email leaks in a hack, nothing meaningful is exposed. No personal data. No recovery accounts. No access to long-term subscriptions.
Reduced Phishing
Fake or disposable emails don’t have behavioral history, making you a much harder target for personalized phishing attacks.
Safe Browsing on Untrusted Websites
Temporary emails offer insulation when:
- Testing new apps
- Downloading free resources
- Signing up for forums
- Joining one-time webinars
- Requesting discount codes
If a site feels shady, don’t trust it with your personal inbox.
4. Real-World Use Cases for using Temporary Emails
The Free Trial Trap
Jenna signs up for a 7-day trial for a video tool. She uses a temporary email, gains instant access, and never hears from the company again after the trial expires. Her real inbox? Untouched.
The Data Leak Non-Event
Mark uses a disposable email for a small e-commerce shop. Six months later, the shop suffers a breach that exposes thousands of emails. Mark doesn’t even remember the disposable address—nothing ties back to him.
Public Wi-Fi Signup Safety
At an airport, Tom needs Wi-Fi. The form demands his email. Instead of using his real email, he uses a temporary email to avoid future spam and tracking.
Download Gates & Lead Magnets
Creators often require an email to access:
- Checklists
- E-books
- Templates
Using a disposable email keeps your personal inbox safe from marketing automation systems.
5. Best Practices for Using Temporary Emails
Perfect Scenarios for Temporary Emails
- Free trials
- Unfamiliar websites
- Online contests
- Downloading resources
- Beta-testing tools
- Wi-Fi form submissions
- One-off support tickets
When NOT to Use Temporary Emails
Avoid them for essential services:
- Banking
- Insurance
- Government portals
- Medical services
- Cloud storage
- Anything requiring account recovery
Bonus Privacy Tips
- Create separate email aliases for different categories (shopping, subscriptions, financial).
- Enable two-factor authentication.
- Regularly check your personal email on “Data Breach Check” (provided by Have I Been Pwned).
- Keep your personal inbox reserved for trusted services only.
6. The Future of Email-Based Privacy
The rise of email masking and privacy tools (Apple Hide My Email, Firefox Relay, Proton Pass aliases) shows a growing trend: users want control over how their email identity is shared.
As data tracking regulations tighten globally, temporary and masked email use will become mainstream—not niche.
Conclusion
Your personal email is one of the most valuable digital assets you have. Using it everywhere online creates long-term privacy and security risks, including spam and phishing to identity exposure and data breaches.
Temporary emails offer a simple, effective shield. They reduce digital footprints, minimize attack surfaces, and give users more control over how their information is shared.
Images generated by Google Gemini.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment