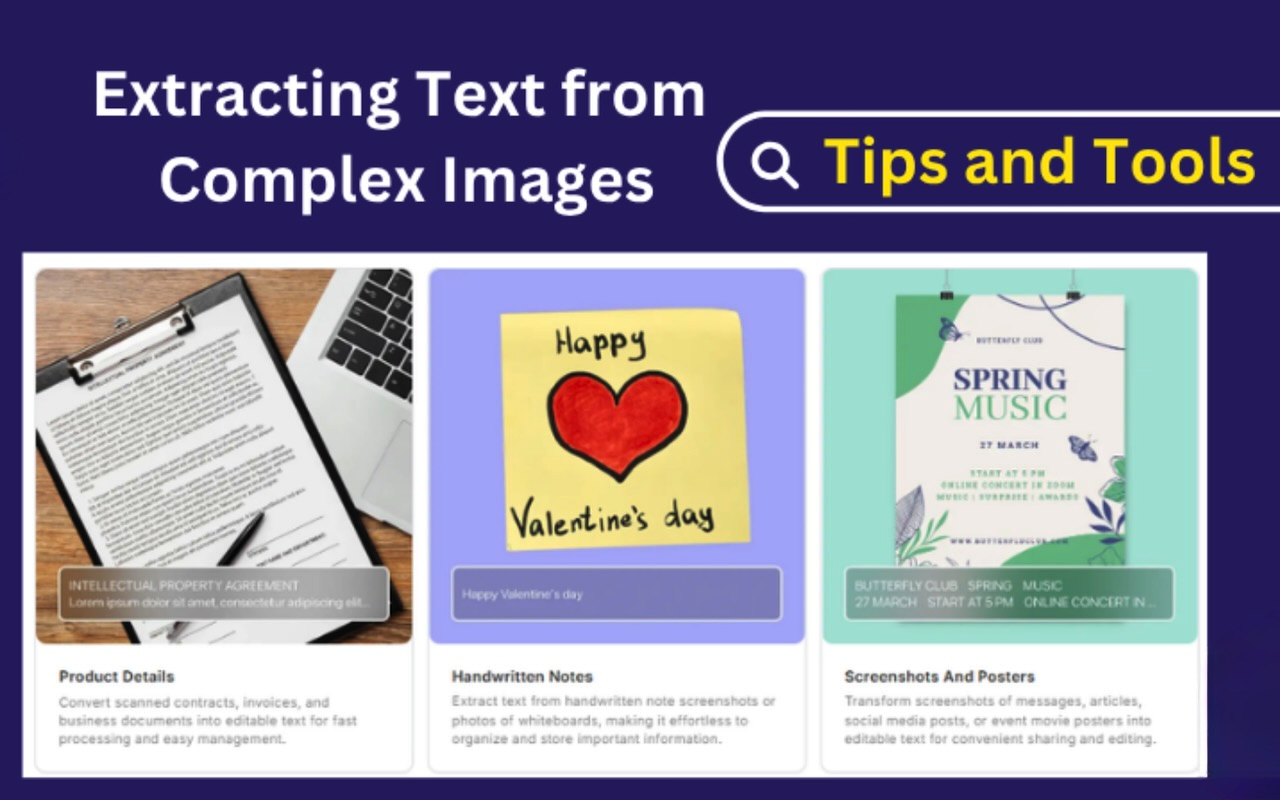
Have you ever tried to photograph a flyer, label, business card, or screenshot, only to have the text turn into an unreadable jumble of fonts, shadows, backgrounds, and irrelevant design components? You enlarge, squint, attempt reading, but it’s effectively impossible to get clean, tidy text without typing it out yourself!
[..]
Read more...