
Ever since we began using computer systems, we are all accustomed to username and password pair to protect our accounts whether that is a computer, bank account, smartphone, or personal email. We also know that password is not the most secure authentication method available today, and there are so many hacks and data breaches that threaten our security. Username and Password are purely based on what the user knows, and this knowledge can be stolen or breached which is a big concern for account security.
To circumvent shortcomings of password credentials, a two-factor authentication (2FA) was invented to protect user accounts. The first-factor authentication is based on a traditional username/password (What you know). The 2FA is a second-factor authentication that is only presented if the first-factor authentication was successful, and it is based on what you are (biometric fingerprint or face ID) or what you have (security key or a device such as Smartphone, Tablet, or Laptop with a fingerprint sensor). 2FA is great for protecting user accounts, but it's time-consuming to use because you have to provide 2 credentials and the second may require typing in a Time-based One-time Passcode (TOTP).
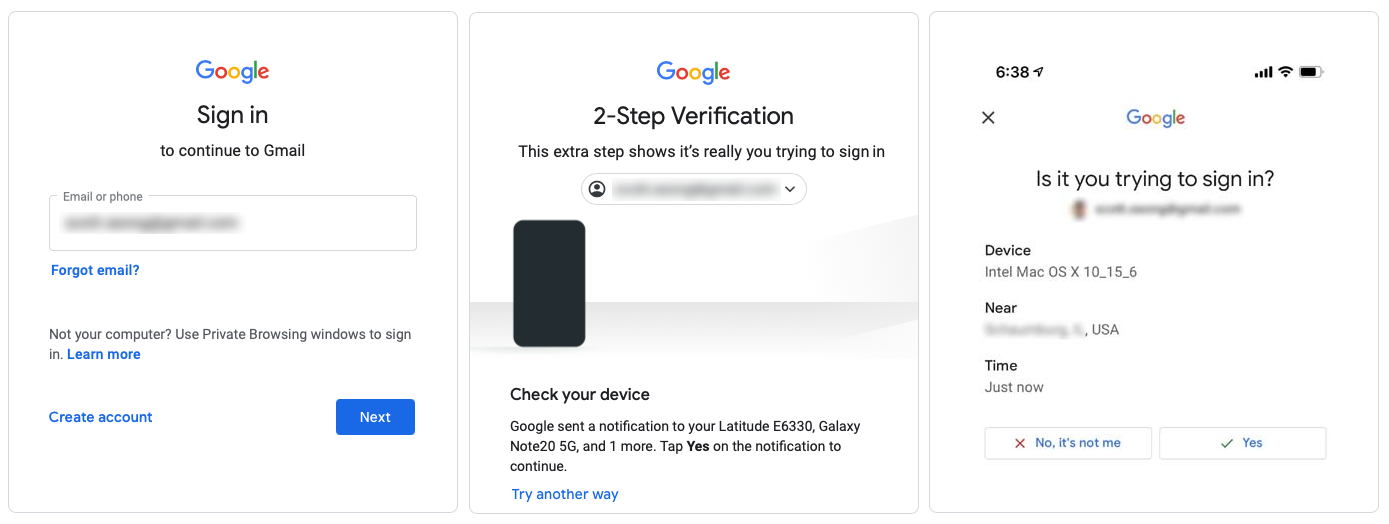
Gmail's 2FA using Webauthn
What is Webauthn?
Web Authentication (WebAuthn) is an industry-standard developed by the W3C and FIDO (Fast IDentity Online) alliance. Members of the FIDO alliance include Google, Microsoft, Apple, Samsung, Yubikey, Mozilla, and many more. The goal of Webauthn is to provide a passwordless authentication system that is secure and easy to use. Webauthn uses Public Key Cryptography (PKC) and simplifies user authentication by using registered devices (what you have).
By utilizing a physical device to authenticate a user, it is much safer than a knowledge-based credential which can be easily stolen either through data breaches, brute force attack or simply from a weak password. With more and more sensitive information being stored online, it is crucial for individuals to safeguard their digital assets with a stronger credential.
There are 3 components that work together to make Webauthn work: web browser, web server, and authenticator (device). All modern web browsers including Google, Safari, Firefox, Microsoft Edge, and Opera do support Webauthn. There is only a handful number of web applications that support Webauthn today (Spring 2021), but this number will grow exponentially in the coming years. The authenticators are physical devices such as YubiKey (Yubico), Titan (Google), U2F (Thetis), smartphones, tablets and laptops supporting Webauthn API.

What is Public Key Cryptography?
Public key cryptography is a protocol that uses two keys (public and private) to encrypt and decrypt data to protect against unauthorized access. The public key is a randomly generated ID that is available for the public to use when encrypting the data. The private key is the secret key that is used to decrypt the data, and it should be kept secret by the authorized person.
Public Key Cryptography is a modern security primitive used in various applications, and it underpins TLS/SSL, S/MIME, PGP, and GPG standards. By using public and private key pair, the server and client can exchange data that can only be decrypted by the known client, and it can also be used in a robust authentication system like Webauthn.
Conclusion
The traditional username and password authentication are vulnerable to hackers and data breaches. The 2FA is great except that it's too time-consuming and not very convenient to use. Webauthn is the new standard that will overcome weaknesses of existing authentication systems, and provide a secure, easy-to-use, and passwordless solution for our everyday authentication.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment