In today's digital landscape, organizations face the challenge of managing access to cloud resources while adhering to data governance and regulatory compliance requirements. AWS Identity and Access Management (IAM) Identity Center provides a comprehensive solution for streamlining access management and ensuring secure and controlled access to AWS resources. Additionally, incorporating privileged access management solutions can further enhance security by safeguarding sensitive accounts and resources.
IAM Identity Center enables organizations to connect their existing identity sources, such as Microsoft Entra ID, Okta, PingID, and others, to streamline access to AWS services. It leverages the System for Cross-domain Identity Management (SCIM) v2.0 standard to keep IAM Identity Center identities synchronized with identities from the Identity Provider (IdP), including provisioning, updating, and deprovisioning users and groups.
By integrating with existing identity sources, IAM Identity Center gains an understanding of an organization's workforce users and groups. This allows identity administrators to assign granular permissions through permission sets, providing fine-grained control over access rights.
Permission sets are a powerful tool for managing access to AWS resources, enabling administrators to define and assign specific permissions to users and groups based on their job functions. Organizations can implement the principle of least privilege, granting users only the minimum permissions required, enhancing security and maintaining compliance with regulatory requirements.
Solution Overview
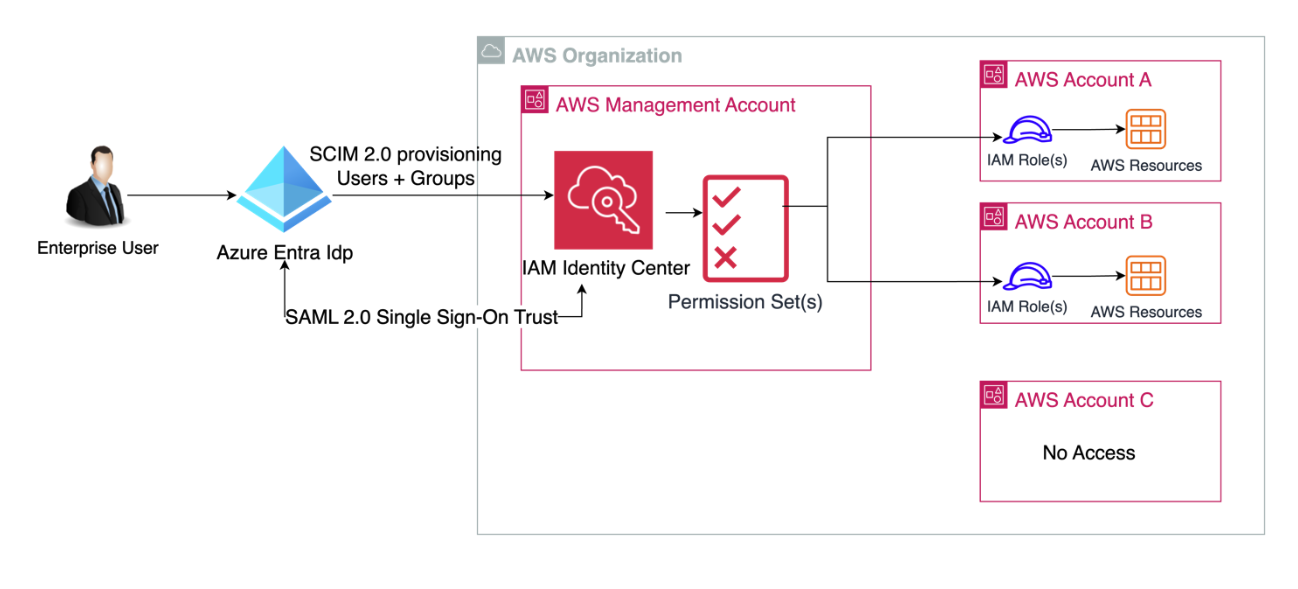
In this solution, we will integrate AWS IAM Identity Center with Microsoft Entra ID, leveraging the System for Cross-domain Identity Management (SCIM) provisioning capability. By setting up an AWS IAM Identity Center enterprise application in Microsoft Entra ID, we can seamlessly synchronize users and groups from Entra ID to IAM Identity Center. This automated provisioning process eliminates the need for manual user and group management, reducing administrative overhead and potential errors.
Furthermore, we will create permission sets within IAM Identity Center and assign them to the corresponding groups provisioned from Entra ID. Permission sets allow for fine-grained control over access rights by defining specific permissions tailored to each group's job functions. This approach ensures that users have the appropriate level of access based on their group memberships, adhering to the principle of least privilege and enhancing security posture. By leveraging permission sets in conjunction with the SCIM integration, organizations can maintain consistent and up-to-date access control across both services, streamlining access management while meeting regulatory compliance requirements.
Pre-requisites
For implementing this solution, we will need:
- An AWS IAM Identity Center enabled account.
- A Microsoft Entra ID tenant.
Identity and Access Management (IAM Identity Center)
In this solution, we will set up an AWS IAM Identity Center enterprise application in Microsoft Entra ID. After that, we will create a group in Microsoft Entra ID, containing one user. The System for Cross-domain Identity Management (SCIM) provisioning feature will automatically push the same users and groups into IAM Identity Center.
Subsequently, we will create permission sets in IAM Identity Center and assign them accordingly.
This process will streamline user and group management by leveraging the System for Cross-domain Identity Management (SCIM) provisioning capability between Microsoft Entra ID and AWS IAM Identity Center.
The creation of permission sets in IAM Identity Center and their assignment to the corresponding groups will make sure that users have the appropriate access rights and permissions based on their group memberships.
By automating this process, you can maintain consistent and up-to-date access control across both services, reducing the administrative overhead and potential for errors associated with manual user and group management.
- Configure SAML (Security Assertion Markup Language) connection and SCIM (System for Cross-domain Identity Management) provisioning between Microsoft Entra ID and IAM Identity Center. Next, create users and groups in Microsoft Entra ID. For this blog, we have created a group named "Data Engineering" with one user, "Silver," belonging to this group.
The screenshot below shows the Data Engineering group created in Microsoft Entra ID under AWS IAM Identity Center Enterprise application.
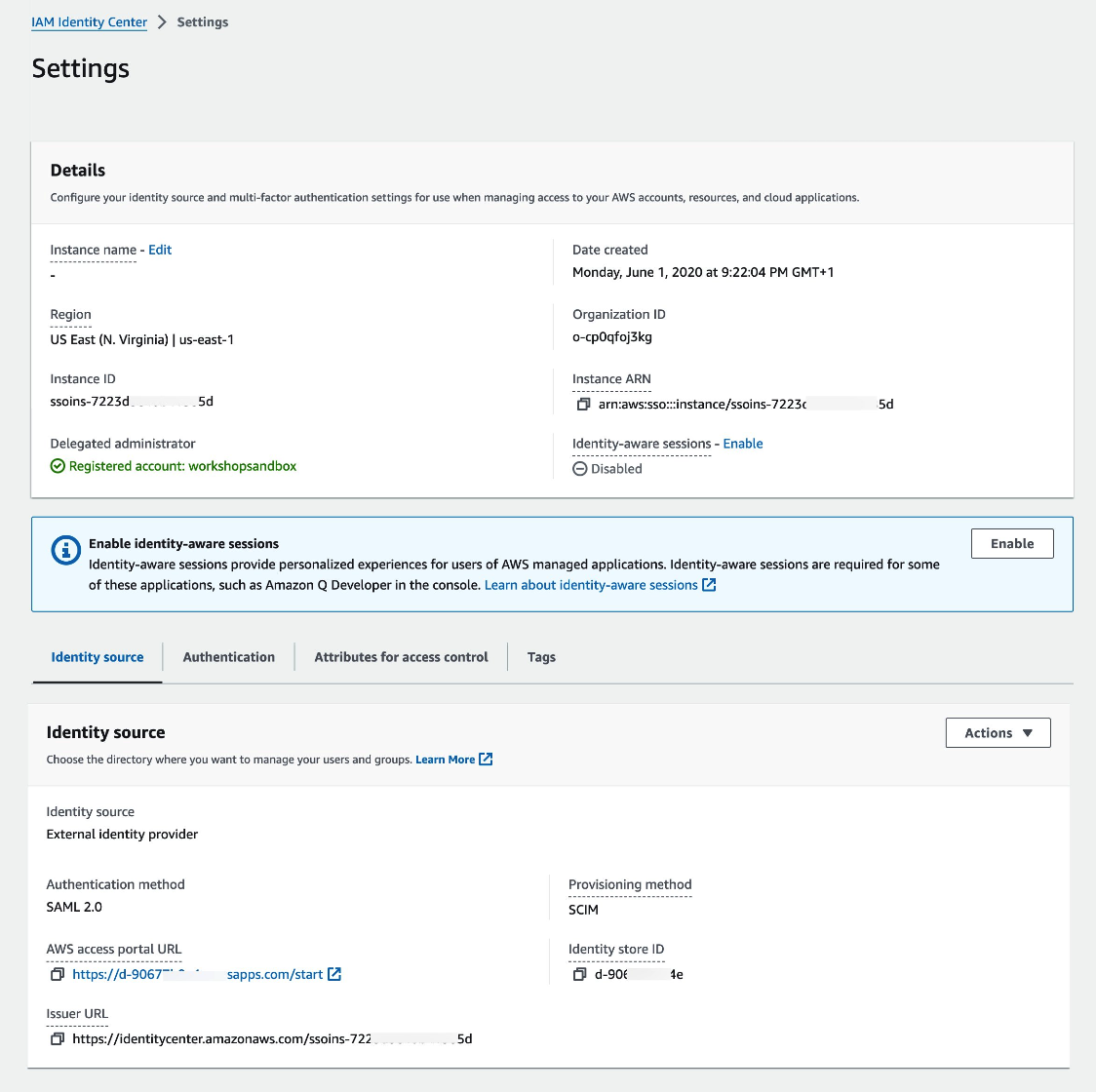
The image illustrates the configuration settings within IAM Identity Center when establishing a SAML connection and SCIM provisioning integration between Microsoft Entra ID and IAM Identity Center.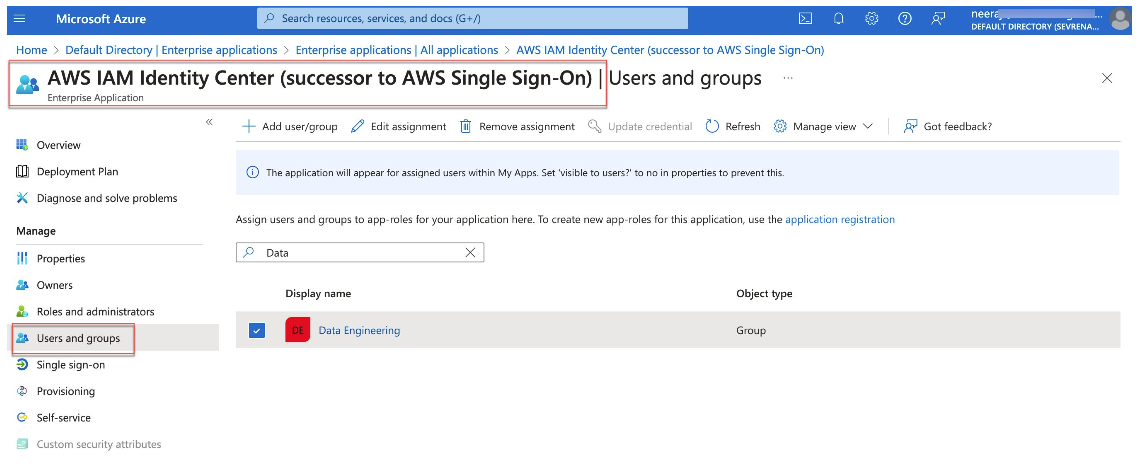
- Microsoft Entra ID provisions the Identity and Access Management (IAM) Identity Centre with the users and groups created in Microsoft Entra ID. We will validate this by examining the groups listed under the AWS IAM Identity Center.
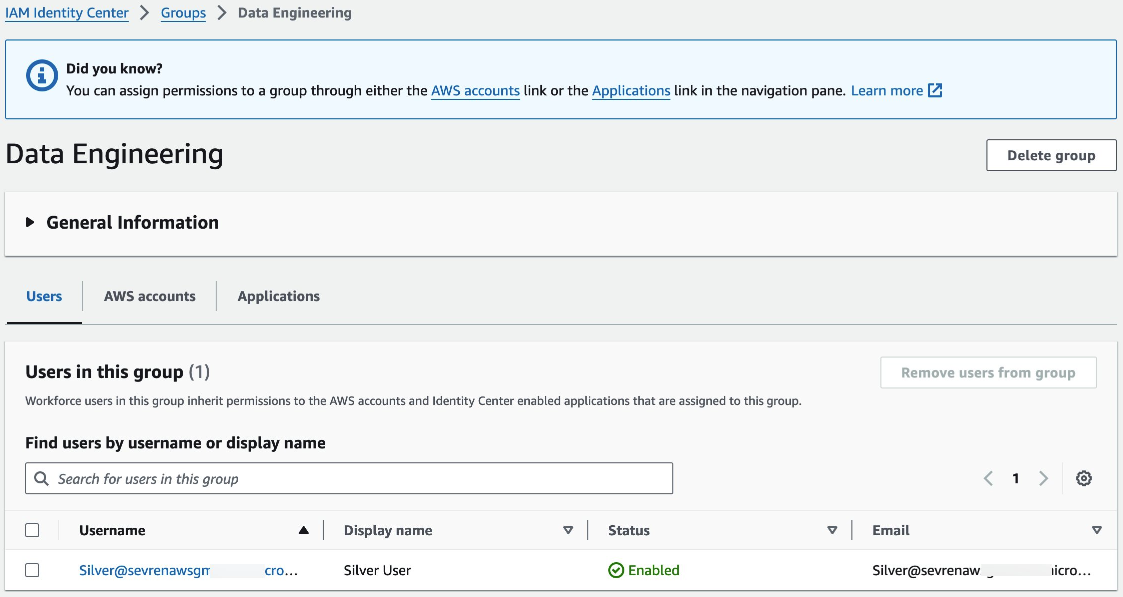
The image depicts a group named “Data engineering” which was originally created in Microsoft Entra ID.
We navigate to the "Data Engineering" group in AWS IAM Identity Center, and we should see the user "Silver."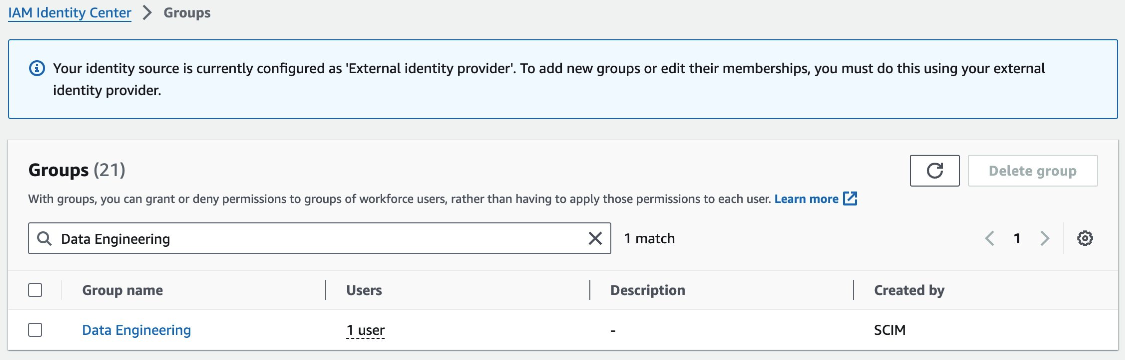
- We will now create a permission set which will be mapped to the enterprise user's job function in IAM Identity Center. This will ensure that your workforce operates within the defined boundaries of permissions you have set for the user.
Navigate to IAM Identity Center →Permissions Sets → Create Permission set.
We will name this Permission Set as “Data-Engineer”.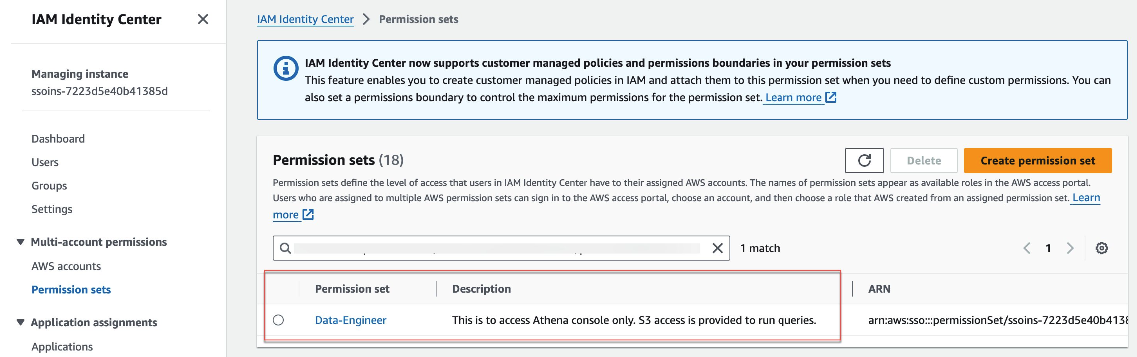
For our blog, let us assume that the Data Engineer Group requires access to Amazon Athena and S3 services. To grant the necessary permissions, we will leverage AWS Managed Policies, which are pre-defined policies offered by AWS. These policies provide a baseline set of permissions for common use cases, ensuring compliance with AWS best practices.
Furthermore, to enhance security controls, we can incorporate Inline policies. This additional layer of access management ensures that users can only operate within the designated boundaries, preventing unauthorized access or actions. - Next, we will assign the "Data-Engineer" permission set to the "Data Engineering" identity group in IAM Identity Center.
We will do this by navigating to IAM Identity Center → AWS Accounts → Select the AWS account.
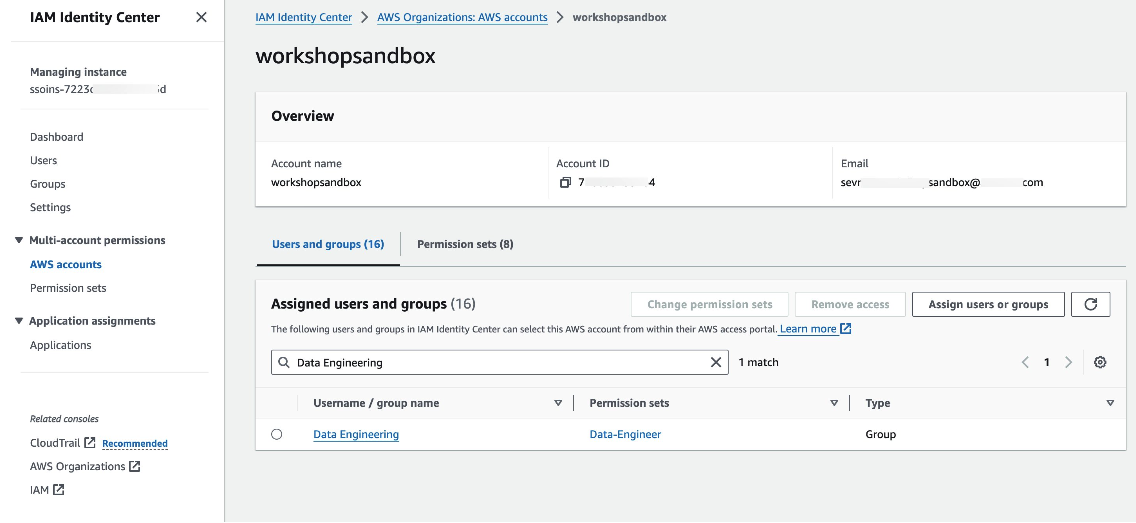
The account name is workshopsandbox in this blog post. We will next click on assign users or groups button and follow along the wizard to choose groups and permission sets.
The image below displays the specific AWS Managed Policies utilized for this blog post.
The image below shows the permission set "Data-Engineer" assigned to the group "Data-Engineering," which has access to the "workshopsandbox" account.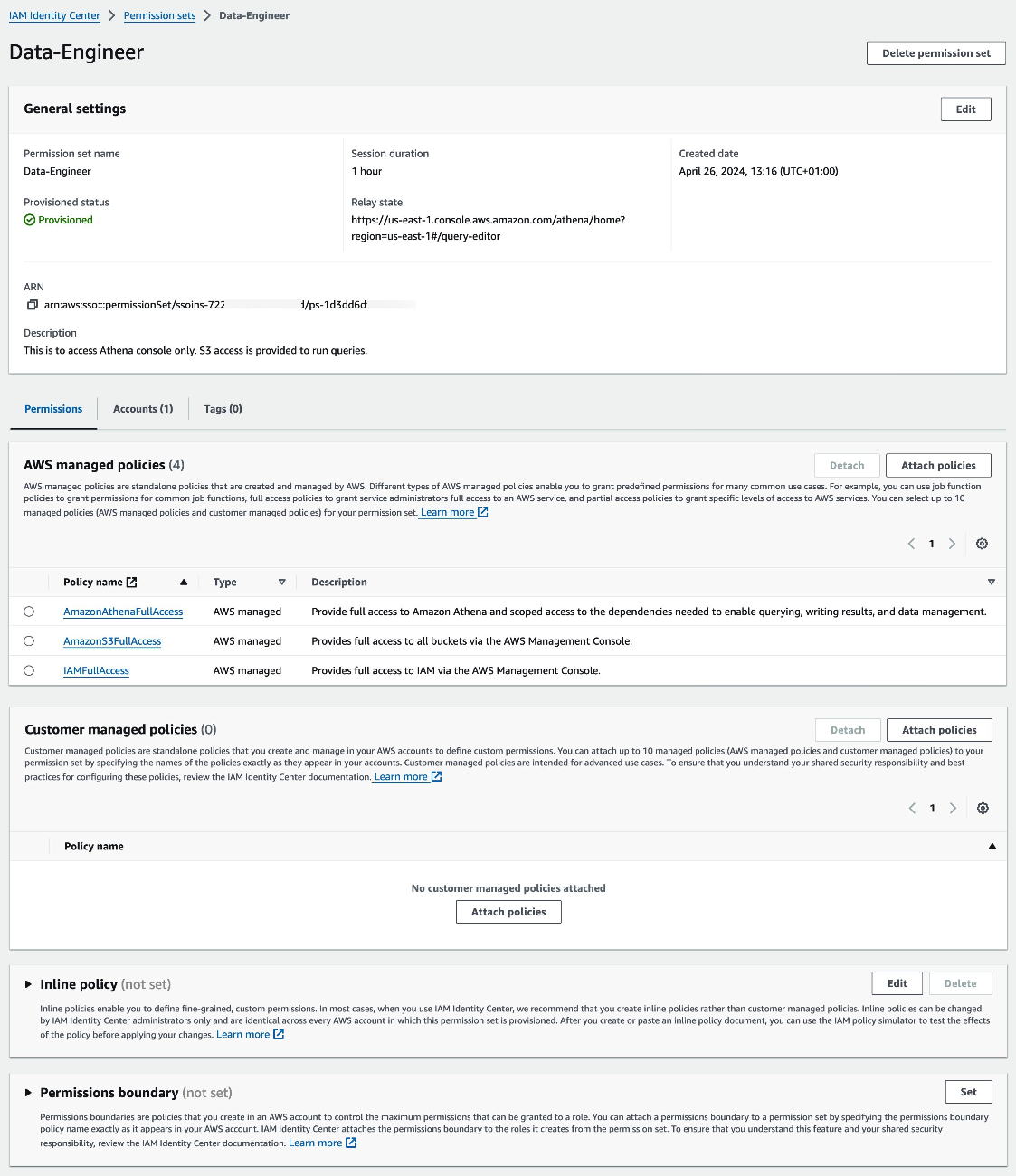
IAM for Education (Identity and Access Management for Education) can be used by educational institutions to manage and control access to digital resources, applications, and services. IAM ensures that only authorized users—such as students, faculty, staff, and administrators—can access specific resources, while also protecting sensitive data and information.
Here’s a breakdown of how IAM works in education:
- User Authentication: Ensures that users (students, teachers, etc.) are who they say they are, typically using usernames and passwords, but can also involve multi-factor authentication (MFA) for added security.
- User Authorization: After authentication, IAM systems determine what each user is authorized to do or access based on their role. For example, a student might only have access to course materials, while a professor might be able to create and grade assignments. Single Sign-On (SSO): One of the key benefits of IAM is simplifying the user experience. With SSO, students and staff can log in once and gain access to all their relevant systems, such as learning management systems (LMS), email, library databases, and more, without needing to repeatedly log in.
- Role-Based Access Control (RBAC): IAM typically uses role-based access control, where permissions are assigned based on roles (e.g., student, professor, admin) rather than individual users. This makes it easier to manage large numbers of users and ensure security.
- Identity Federation: Many educational institutions partner with external systems (e.g., cloud platforms, third-party tools). Identity federation enables users to access these external systems without needing separate credentials, streamlining the process.
- Security and Compliance: Given the sensitive nature of student data (e.g., grades, personal info), IAM helps ensure compliance with privacy regulations (like FERPA in the U.S.) and protects the institution’s resources from unauthorized access.
Overall, IAM for education helps institutions improve security, streamline access, and enhance the user experience for both students and staff.
Conclusion
By integrating Microsoft Entra ID with AWS IAM Identity Center and leveraging the SCIM provisioning capability, organizations can streamline user and group management while maintaining consistent and up-to-date access control.
The creation of permission sets and their assignment to corresponding groups ensures that users have the appropriate access rights and permissions based on their job functions and group memberships.
This solution provides a robust and secure approach to enterprise access management in regulated industries, ensuring compliance with regulatory requirements while minimizing administrative overhead.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment