
Secure online payments are one of the top priorities for businesses handling customer transactions. Given the multitude of cyberattacks and possible data breaches, companies must be on the alert and implement robust security measures. Neglecting this will lead to serious consequences, such as loss of customer trust, reputational damage, and legal complications.
How can you maintain a safe online payment process? Read this article to learn about the potential hazards and actionable tips for tackling them to protect your business and clients.
Digital Payment Risks Looming Over Businesses
With the rise of cashless transactions, cybercriminals have also stepped up their attacks. According to a report from Accenture, digital fraud jumped by 31% from 2020 to 2021. Hackers leverage the latest technologies to crack the code in online systems and access sensitive customer information.
Despite the convenience of digital payment methods, businesses and consumers alike are still wary of their security. The main risks associated with these payment modes include:
Phishing scams
This type of fraudulent activity is rather widespread. Hackers send scam emails, text or voice messages, or make phone calls on behalf of a familiar and trusted company. Their main goal is to trick people into downloading malware or following links to scam websites designed to steal personal and financial information.
Verizon’s 2023 findings show: nearly 36% of all data breaches stemmed from phishing scams. According to Statista, global internet portals ranked first among organizations targeted the most by phishing in 2023, closely followed by web services, online stores, and banks.
Malware
Cyber attackers design malicious software, or malware for short, to gain unauthorized access to any device or network. Typical examples of malware include Trojan viruses, worms, spyware, ransomware, and adware. These programs are developed to cause havoc and intercept sensitive information. They can infiltrate systems through emails, scam links, infected files, and malicious websites.
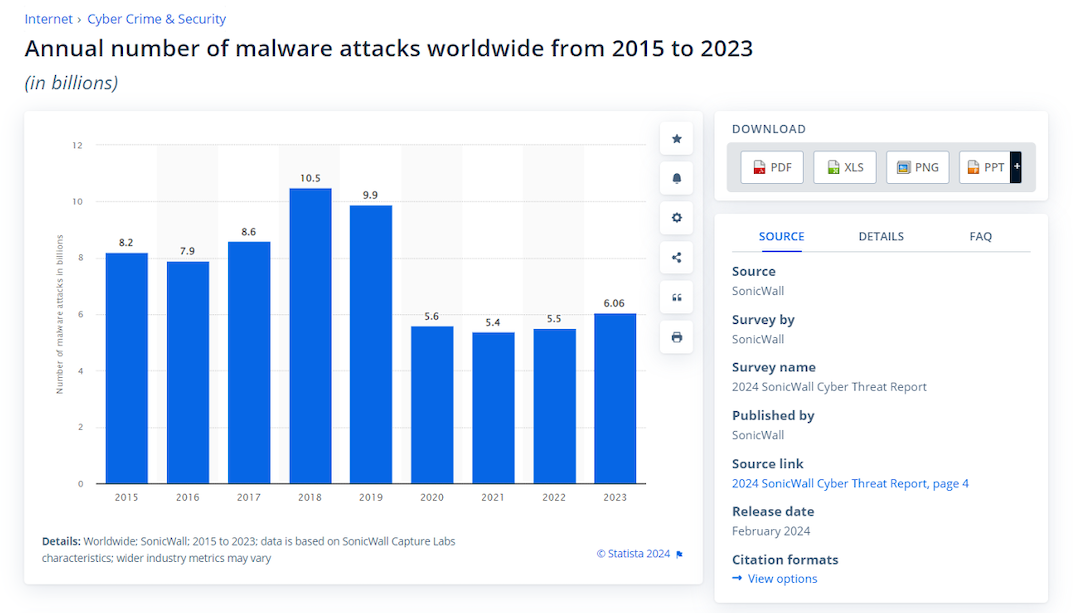
Image Source Statista
In 2023, malware instances increased by 10 percent compared to the previous year, hitting a whopping 6.06 billion. Meanwhile, 2018 recorded the highest number of malware attacks, at 10.5 billion globally.
Reliance on third-party vendors
As a rule, businesses handling online payments outsource crucial functions to third-party service providers, such as payment processors, POS (point-of-sale) system vendors, payment gateway providers, etc. This certainly enhances efficiency but, at the same time, introduces potential security risks.
According to a 2022 research by the Ponemon Institute, third-party attacks have grown from 44% in 2021 to 49% in 2022. The key reasons for such an upward trend result from the following:
- Limited implementation of access governance and access visibility systems;
- Excessive privileges granted to vendor accounts;
- Disregard of access control methods, such as access notifications and approvals, Zero Trust Network Access, multifactor authentication, and so on;
- Insufficient monitoring of third-party vendors’ activities within the company’s network.
Organizations shouldn’t go solely by trust and reputation when allowing access to third-party vendors. Gauging the vendor’s security measures and compliance standards, as well as taking a smart approach to managing access, can significantly mitigate possible risks of data breaches or other safety hazards.
For the record: Beyond payment-specific operations, access controls are crucial for all business processes dealing with sensitive data. Let’s take the CPQ (configure-price-quote) part of the sales cycle as an example. Without properly setting up access controls, critical information, such as customer pricing, product configurations, and sales quotes, can be misused.
In this context, implementing the right tools can prevent data breaches and save business reputation and resources. The numerous benefits of Salesforce CPQ make it a valuable solution for sales teams to automate workflows and maintain data integrity and security due to robust access management features.
Secure Payment Methods for Online Transactions

Fast, secure, and frictionless transactions have become the new norm in our digital reality. People are used to ordering food, shopping for clothes, or booking holidays with just a few taps on their smartphones. However, whenever users pay online, hackers may compromise their sensitive information, such as bank account and credit card data or personal identification numbers.
With a variety of payment options, businesses must not only cater to diverse customer needs but prioritize reliable and efficient solutions. Safe payment methods will keep clients happy and foster trust in the brand. Below, we’ll highlight the top choices for a company to consider.
Credit cards
This popular online payment method balances convenience with security for consumers and merchants alike. Credit card companies adopt advanced security features like 3D secure protocols, encryption, and transaction monitoring. When detecting unusual patterns, they might block the account to prevent fraud.
Most of the time, credit card issuers have your back in case of theft or misuse. They may limit your liability to a low amount or not charge you at all. Besides, there are laws and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) or the US Fair Credit Billing Act (FCBA), providing additional protections for credit cardholders.
E-wallets
Digital wallets, also known as e-wallets, are applications designed to store various credentials, such as credit/debit card and bank account details, personal identification numbers, loyalty card information, receipts, etc., and allow users to make online purchases without constantly entering their payment data.
PayPal, Apple Pay, and Google Pay are popular examples of digital wallets. This payment method offers multiple security features to ensure safe transactions:
- Tokenization protects users' sensitive data, like credit/debit card information, by encoding and storing it as unique and randomly generated 15-16 digit numbers called tokens.
- Multifactor authentication includes several verification steps, such as fingerprint/facial recognition and entering a PIN when users log in or make a transaction.
- Consistent fraud monitoring involves keeping tabs on transactions in real time and notifying users of suspicious activities.
SWIFT and ACH Transfers
These types of electronic transactions are suitable for moving funds between banks. An ACH (Automated Clearing House) payment is commonly used in the US. It employs tokenization and encryption and follows strict rules and regulations to protect account and payment information.
SWIFT (Society for Worldwide Interbank Financial Telecommunication) is a messaging network that links multiple financial institutions and facilitates international money transfers.
SWIFT uses a reliable system of codes so only authorized banks can access transaction data.
Best Practices for Secure Payments Online

Since malicious actors incessantly seek new ways to steal sensitive customer payment data, businesses must be well-versed in diverse cybersecurity practices to promote a safe online payment environment. Let’s review the top seven tips on protecting financial transactions from hazards and boosting customer confidence.
1. Set up an SSL certificate
SSL (secure sockets layer) is a surefire means of improving payment security for businesses. Installing an SSL certificate on a website ensures all data remains encrypted and secure during transmission, giving customers peace of mind when submitting personal and financial details.
Numerous types of SSL certificates are available, each serving a specific purpose and providing different levels of security. The list includes domain-validated (DV), organization-validated (OV), multi-domain, wildcard, and extended validation (EV) SSL certificates.
The latter option is best for eCommerce sites, online banking platforms, or any website that handles sensitive customer data. To get an EV certificate, companies are required to go through a detailed validation process. This process involves verifying their legal identity, domain ownership, and more.
2. Be PCI DSS compliant
The Payment Card Industry Data Security Standard (PCI DSS) compliance is a necessary prerequisite for businesses processing, storing, or transmitting sensitive cardholder information. PCI DSS entails a set of security guidelines, a total of 12, that organizations must follow to maintain a safe online payment experience. Some of these requirements include:
- Installing firewalls. They work as a first line of defense and monitor incoming and outgoing traffic to thwart unauthorized access.
- Adopting strong password policies: using long and complicated passwords, updating them regularly, changing vendor-supplied defaults for system passwords and other security settings.
- Protecting cardholder data, namely storing it to a minimum, removing it quarterly, and applying stringent access control measures.
- Encrypting transmitted cardholder details so they’re not compromised while being transferred over open networks.
- Updating antivirus programs and testing security systems for vulnerabilities regularly to fend off the latest security threats efficiently.
3. Verify transactions
Since paying online relies on card-not-present transactions, businesses must go the extra mile to safeguard customers’ sensitive financial data and mitigate fraudulent activities. Here’s what they can do to amp up security:
- Check the CVV (Card Verification Value) during an online checkout process. In case of a mismatch, the transaction should be declined.
- Confirm the given email address is valid through a verify email address tool. This service sifts through databases and public records and helps companies verify if an email is authentic.
- Cross-check a user’s location with shipping information. A legitimate transaction typically has the same billing, shipping, and IP details. If there are considerable discrepancies, it’s wise to request additional ID proof, like a photo of a driver’s license or passport, or verify through a phone call.
- Leverage proxy piercing techniques. They can tell whether users mask their IP address, geolocation, or other identifying information.
4. Implement multi-factor authentication (MFA)
Think of MFA as an extra layer of security to ward off a data breach. The process involves utilizing numerous authentication methods beyond passwords, namely biometric recognition, one-time codes sent over an email/SMS, or security questions. For instance, online store owners running business on an eCommerce platform have to be extra careful about their admin accounts.
If hackers manage to steal login credentials, loads of sensitive customer and transaction data could be compromised or stolen, leading to serious financial losses and reputational harm. With multi-factor authentication in place, cyber criminals’ login attempts will fail. They simply won’t be able to go through additional security barriers imposed by MFA.
5. Invest in cyber insurance
Even the strongest security measures cannot fully protect businesses from savvy hackers or accidental data breaches. Adopting cyber insurance policies can be useful in such situations.
Cyber insurance covers financial expenses companies may incur as a result of ransomware attacks, data breaches, or other security incidents.
These costs may become a heavy burden on a business's bottom line. For example, the average ransomware attack sets a company back USD 4.54 million on top of any ransom payments. With the growing number of security threats, businesses are recognizing the importance of investing in cyber liability insurance. The ascending trend of the global cyber insurance market size attests to it.
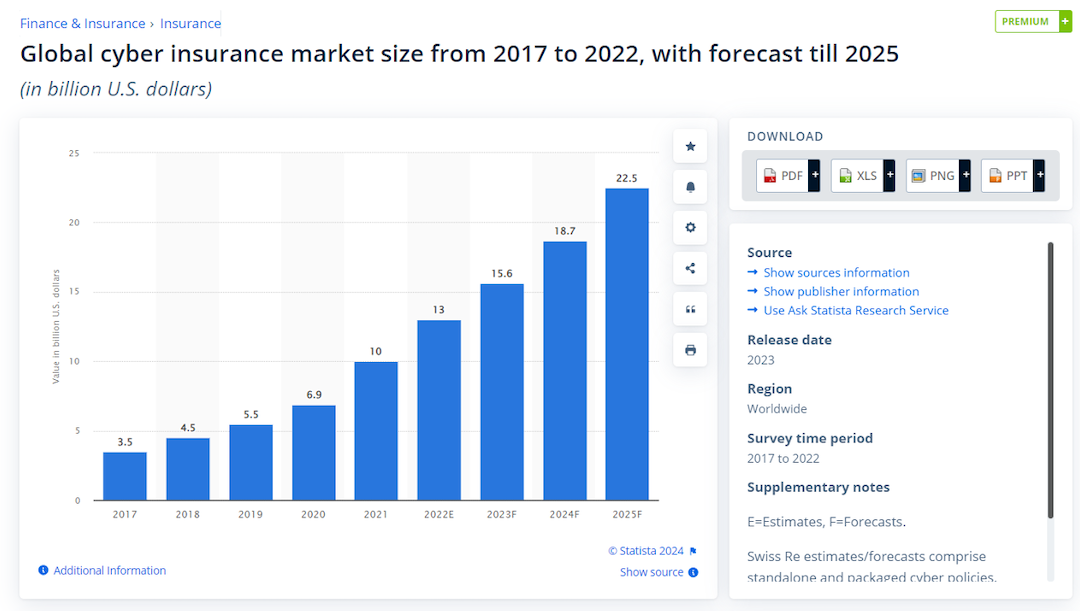
Image Source Statista
6. Accept a secure online payment method
More businesses are ditching traditional cash transactions in favor of online payment methods, such as digital wallets, credit cards, mobile payment apps, and more. In 2023, digital wallets accounted for nearly half of global e-commerce payment transactions. Meanwhile, credit cards came in second with a 22% market share.
With diverse payment solutions, businesses can accommodate a wide range of customer needs and preferences. Yet, it’s essential to opt for secure payment methods to protect customer data and ensure safe transactions. Above, we highlighted the best forms of paying online.
7. Train employees in online payment security
Hackers may take advantage of trustful and unaware employees to breach critical systems and devices. Therefore, it's a great idea to educate staff members on the best online payment security practices. Keep them informed about possible cyber threats that may arise and teach them how to spot and handle them.
Develop a comprehensive program that addresses multiple aspects of online payment security, including safe browsing behavior, password generation, and data access controls. Make use of simulation exercises to help your team put theory into practice and learn how to respond to security threats.
Promote Secure Online Payment Processing
Secure online payment experience is of utmost importance for businesses striving to foster customer loyalty and stay ahead of the competition. With the growing number of cyber attacks, companies must adopt effective techniques to protect customer data and ensure secure financial transactions.
We’ve listed down seven practical tips to help businesses stay one step ahead of malicious attacks, from setting up SSL certificates and enabling multifactor authentication to purchasing cyber insurance and educating employees about possible threats. Opting for secure online payment methods is equally important. All in all, taking these steps creates a safe online payment environment for both businesses and clients, minimizing the risks of fraudulent transactions and data breaches.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment