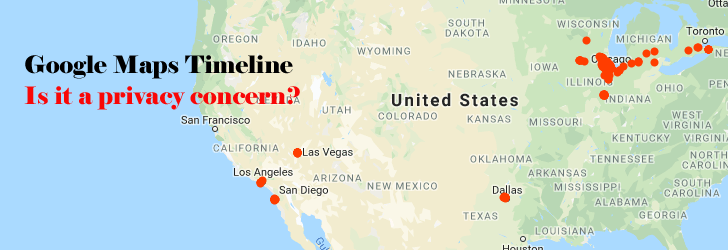
Most smartphone users may not know this, but Google has been tracking your locations and routes you took to go place to place. Unless you have intentionally turned off the location history settings, Google has been keeping track of your locations from the moment you own your smartphone. It may be mind-boggling for some users, but Google advertises it as a free service offered you to help track your location history. The service is available on both desktop and mobile users, and you can edit, delete or disable location history in your timeline. Your location timeline is private, so only you can view it after logging into Google account. To view your location history, you may visit










