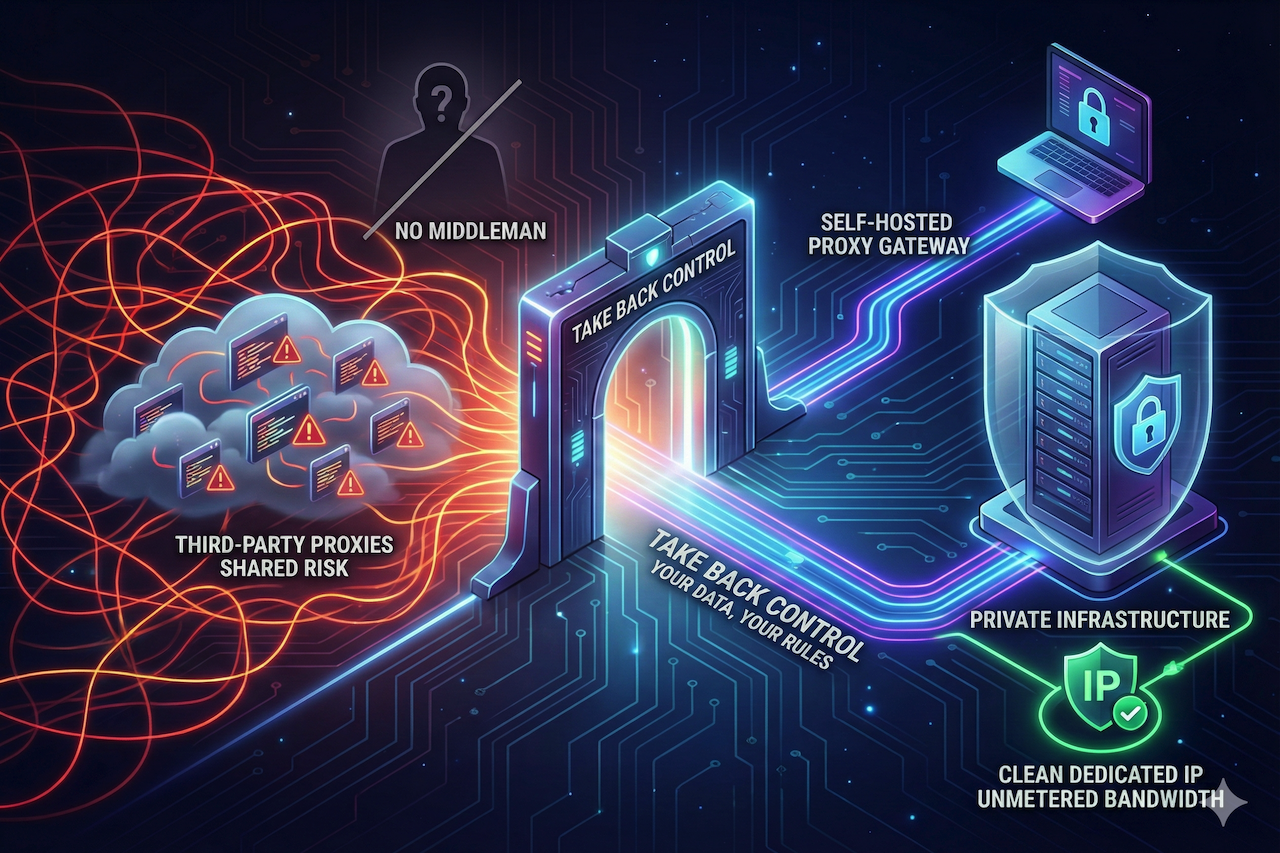
Whether you are masking your digital footprint, managing social media accounts, or gathering competitive intelligence, you need an intermediary IP address. The market is flooded with providers selling "premium" proxy pools, rotating residential IPs, and datacenter proxies. However, relying on third-party proxy providers introduces a paradox: to achieve anonymity, you are handing over your traffic data to a stranger. In 2026, the most security-conscious professionals are realizing that the only proxy you can truly trust is the one you build yourself.
This is where the concept of the "Self-Hosted Proxy Gateway" comes into play. Instead of renting an IP address that has been used by thousands of others (and potentially flagged by anti-abuse systems), you deploy your own private endpoint on a clean, high-performance virtual private server. Providers like MVPS offer virtual private servers with dedicated IP addresses and KVM virtualization are often used for this strategy. These environments provide isolated resources and clean IP space, allowing users to deploy their own private endpoints without inheriting usage history from shared proxy pools. Rather than relying on IPs that may have been previously used by multiple parties, a self-managed VPS gives full control over the server environment and its network reputation.
Eliminating the "Man-in-the-Middle" Risk
The fundamental flaw of commercial proxy services is visibility. When you route your traffic through a third-party provider, they technically have the ability to inspect your data packets. Even if they claim a "No Logs" policy, you are operating on blind trust. If their infrastructure is compromised, or if they decide to monetize your browsing habits, your privacy is null and void.
By setting up your own proxy server (using software like Squid, Dante, or 3proxy) on your own VPS, you eliminate the middleman. You become the network administrator. You control the logs (or lack thereof), the encryption protocols, and the authentication methods. This creates a closed loop of trust where the only entities seeing your traffic are you and the destination server. For businesses handling sensitive market research or proprietary data, this chain of custody is essential.
The Battle for Clean IPs and Reputation
In the niche of IP reputation, not all addresses are created equal. Commercial datacenter proxies are often sold and resold to hundreds of users. One user might use the IP for legitimate SEO auditing, while the next might use it for spamming. As a result, when you try to use that IP, you are greeted with endless CAPTCHAs, Cloudflare blocks, or Access Denied screens. You are suffering for the sins of the IP's previous renters.
A dedicated VPS offers a static, dedicated IP address that is yours alone. This allows you to warm up the IP and maintain a spotless reputation. Major platforms (like Google, LinkedIn, or Instagram) are far less likely to flag traffic coming from a stable, consistent IP address than from a volatile, rotating proxy pool known for abuse. With an MVPS solution, you have the stability required to build long-term trust with the services you interact with.
Unmetered Bandwidth vs. Cost-Per-Gigabyte
Have you looked at the pricing models of premium proxy providers lately? They often charge per gigabyte of data transferred. If you are running high-volume scraping tasks, video stream analysis, or heavy file transfers, the costs can skyrocket exponentially. You find yourself rationing your bandwidth to save money, which stifles your operations.
A VPS flips this economic model on its head. Most professional VPS plans come with generous bandwidth allocations or unmetered traffic ports at a flat monthly rate. You can push terabytes of data through your private proxy gateway without worrying about overage fees. You get enterprise-grade throughput, often 1Gbps or more, dedicated to your connection. This means lower latency, faster scrape times, and a predictable bill at the end of the month, regardless of how heavy your traffic load is.
Custom Protocols and Granular Control
Commercial proxies usually offer a "take it or leave it" configuration, standard HTTP/HTTPS or SOCKS5 on a random port. But what if you need more? What if you need to implement strict IP whitelisting so only your office can access the proxy? What if you want to run a WireGuard VPN tunnel alongside your SOCKS5 proxy for a hybrid security setup?
Owning the underlying VPS gives you Root Access, which means total configurability. You can tweak the TCP/IP stack for lower latency, set up custom firewall rules to block specific user agents, or implement advanced authentication chains. You can even run headless browsers (like Puppeteer or Selenium) directly on the server to handle JavaScript-heavy sites that standard proxies can't manage. You are building a bespoke tool tailored exactly to your workflow, not adapting your workflow to a limited tool.
Defense Against Traffic Correlation
Finally, building your own infrastructure allows for better defense against traffic correlation attacks. In a shared proxy environment, sophisticated adversaries can sometimes correlate traffic patterns to identify the original user. When you control the VPS, you can implement traffic shaping, padding, or multi-hop chains (chaining multiple VPS instances together) to obfuscate your footprint further. You can deploy instances in specific geo-locations required for your tasks, ensuring that your digital presence appears exactly where you need it to be, with a hardware signature that looks like a legitimate server rather than a transient proxy node.
Final Words
Take back control of your digital footprint. Stop renting dirty IPs and start building your own private, secure proxy infrastructure.
Featured Image generated by Google Gemini.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.






Comments (0)
No comment