
Cybercriminals have found a new way into your business: QR codes. Disguised in invoices, posters, or emails, these codes can quietly redirect employees to phishing sites designed to steal credentials or drop malware without raising any red flags.
Let’s take a closer look at how these attacks work, and how you can quickly detect and stop them before they cause real damage.
The Real Dangers of QR Code Hacker Attacks
Unlike a suspicious link in an email, a QR code hides its destination until it’s scanned, making it easy for attackers to disguise malicious content as something harmless.
- Fake login pages: A QR code might lead to a spoofed Microsoft 365 or Google sign-in page, tricking employees into handing over credentials.
- Malware downloads: Scanning the code can trigger the download of spyware, trojans, or info-stealers, especially on mobile devices with weaker security controls.
- Bypassing email filters: Since the code is embedded in a physical or image-based format, it often slips past traditional email security tools.
- Social engineering: Attackers often add urgency or context; "View updated invoice" or "Scan to reschedule your delivery" to increase the chances of a scan.
For businesses, even one compromised device can lead to unauthorized access, data theft, or a larger breach.
Real-World Example: Analyzing a Malicious QR Code in Seconds
QR code attacks are dangerous because the real threat is hidden. You don’t see the link, and by the time you do, it might already be too late. That’s why sandboxes with automated interactivity, like ANY.RUN, are so valuable.
When you turn on this feature, it can automatically detect a QR code inside a file, extract the hidden link, and open it to see what’s really there, all on its own. And because everything happens inside a secure virtual environment, there’s no risk to your systems.
Let’s look at a real example of how a QR attack unfolds and how the sandbox catches it.
View analysis session with QR attack
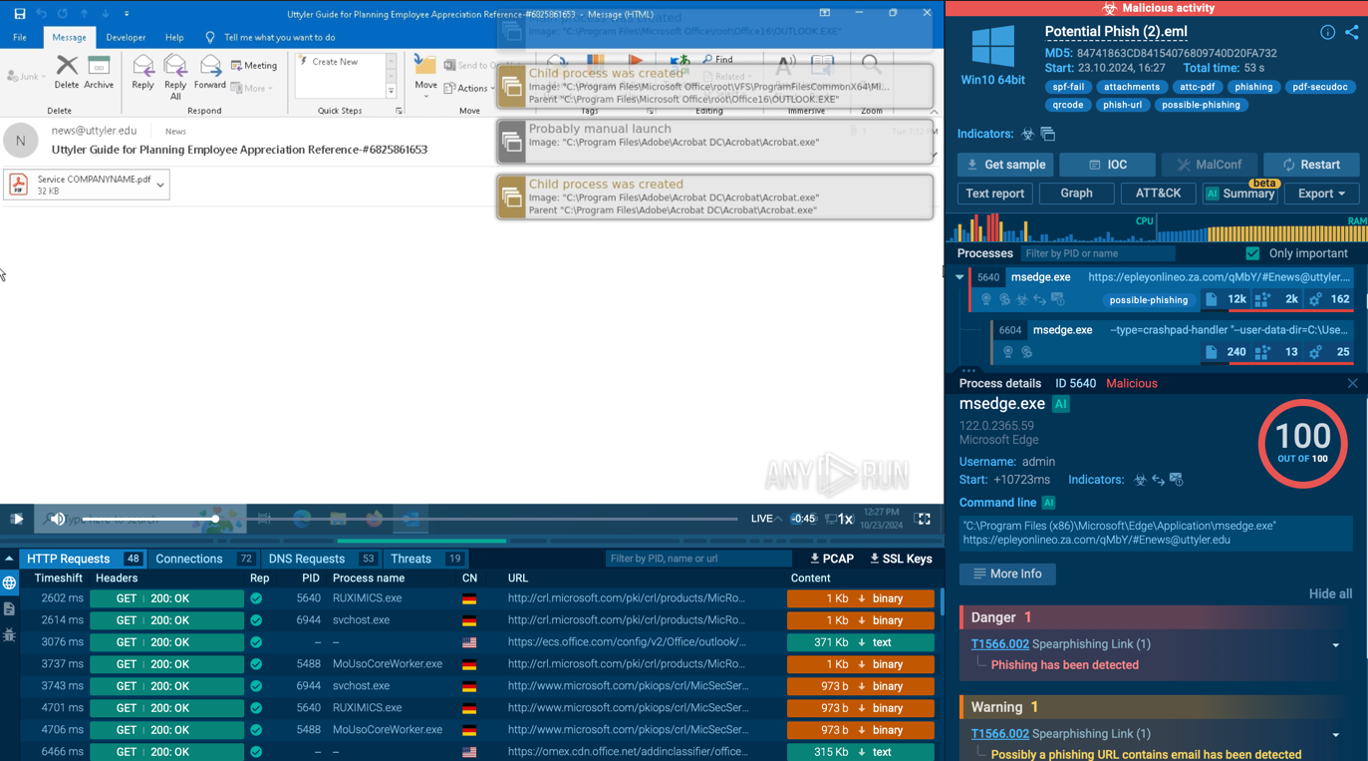
Phishing attack analyzed inside ANY.RUN sandbox
In this case, the attack started with a phishing email that had a PDF attachment. On the surface, nothing looked suspicious, but inside the PDF was a QR code hiding a malicious link.
Stop threats before they compromise your company. Proactive sandbox analysis, as supported by services such as ANY.RUN, helps reveal hidden threats before they escalate.
Here’s how the sandbox uncovered the threat:
1. The email file was uploaded and analysis started.
Automated Interactivity was enabled before launch. The sandbox instantly began simulating user actions.
2. The sandbox opened the email and accessed the attached PDF.
Just like a real user would, it opened the file in a virtual Outlook environment and then viewed the PDF.
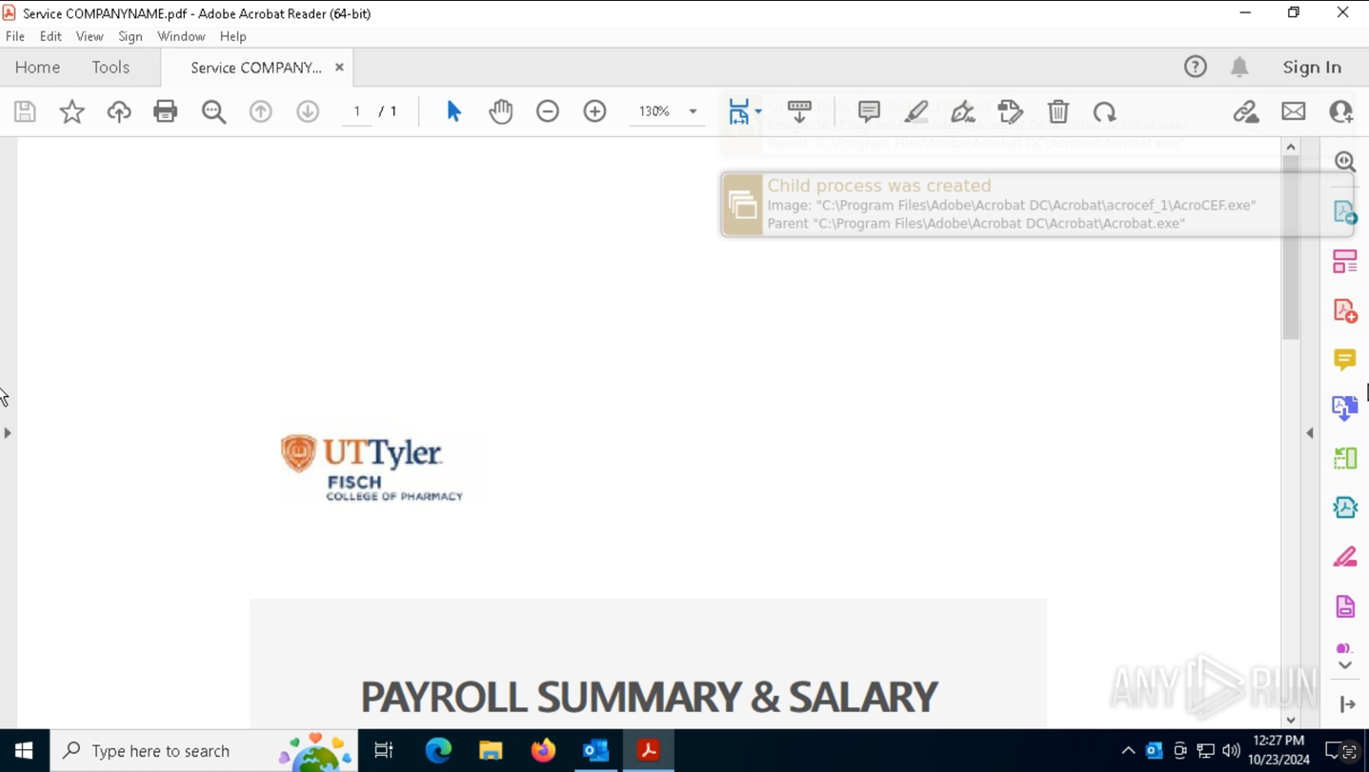
PDF file accessed inside a safe sandbox environment
3. The QR code was detected and scanned.
The sandbox recognized the QR code inside the PDF, automatically extracted the hidden URL, and opened the link in a browser.
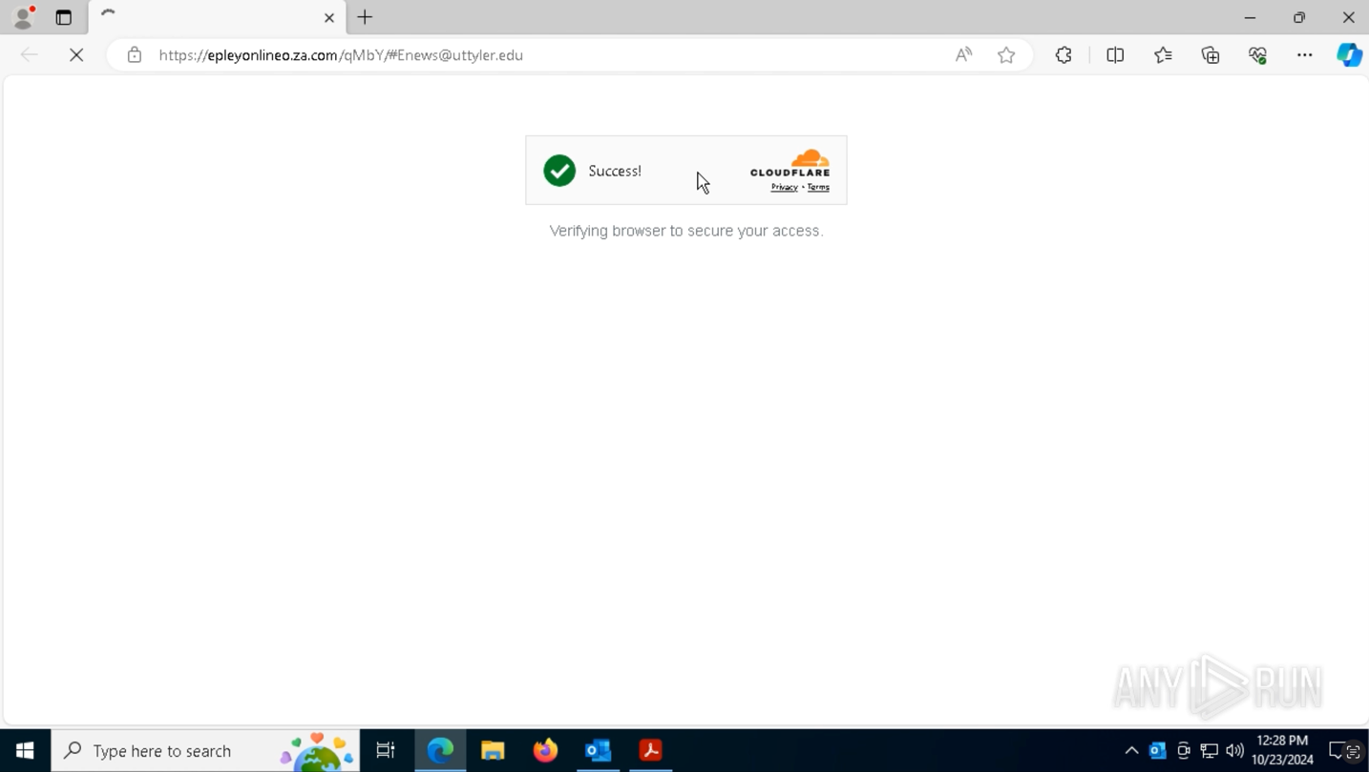
Malicious link opened automatically inside ANY.RUN sandbox
4. It encountered a CAPTCHA and solved it.
The page included a CAPTCHA to avoid automated tools, but the sandbox handled it and moved forward without stopping.
5. The final phishing page was loaded and flagged.
Once the page fully loaded, the sandbox identified it as a phishing site, tagged the session as malicious, and displayed all related activity for further investigation.
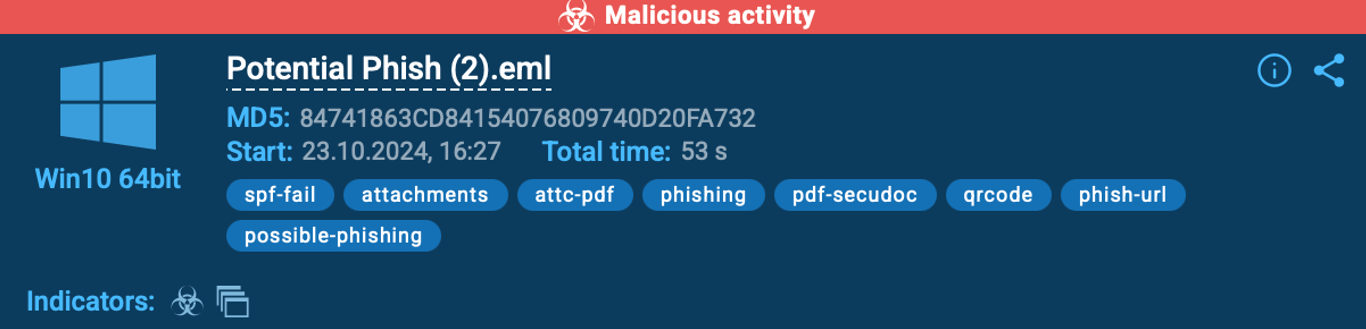
Why Interactive Sandboxing is a Game-Changer for QR-Based Threats
Most businesses aren’t prepared to deal with QR-based phishing attacks. These threats often bypass traditional security tools because the malicious link is hidden until the QR code is scanned and by then, the damage may already be done.
That’s where ANY.RUN’s interactive sandbox with Automated Interactivity brings real value. It doesn’t just analyze files. It acts like a real user, scanning the QR code, opening the link, solving basic interactions, and exposing what’s behind it, all inside a safe environment.
Here’s why it matters:
- Reveal hidden links before anyone scans them
- Understand the full context of the threat, including fake pages or malicious downloads
- Give your SOC team clarity without spending time on manual steps
- Protect your employees from phishing sites that would otherwise go unnoticed
- Respond faster and make smarter security decisions with concrete evidence
QR code attacks are subtle, but they don’t have to be a mystery.
Conclusion
QR code-based attacks are a growing threat that exploit the trust and convenience of quick scans to bypass traditional security defenses. Disguised as routine communications, these codes can quietly lead users to phishing sites or trigger malware downloads without immediate detection. By incorporating interactive sandboxing into your security workflow, you not only stay ahead of emerging threats but also equip your team with the visibility and confidence to respond decisively.
Featured Image by Freepik.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment